A practical guide to combining MCP, ACP, and A2A to build modular, secure, and collaborative AI agent systems
AI agents are no longer just tools on standby. They’re evolving into distributed teams, each with specialized roles, secure access paths, and clear boundaries.
Imagine you’re building a system where one agent breaks down a user’s request, another executes each task, and a third validates the output against internal policy. Each agent may use different protocols, tools, and expectations around data, roles, and security. There’s no single standard to make this orchestration seamless. But combining the strengths of existing protocols; MCP, ACP, and A2A, gets us close.
This post outlines a structured approach for integrating these protocols to build reliable, modular, and secure agent systems.
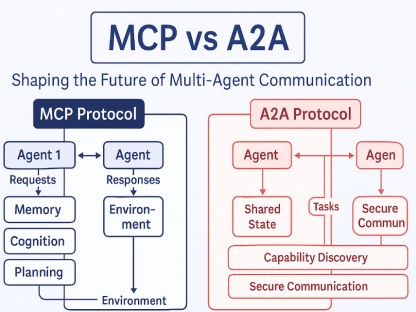

Understanding the Landscape: Three Key Protocols
1. Model Context Protocol (MCP)
MCP was developed to give large language models (LLMs) secure, structured access to tools. It’s like an OpenAPI manifest for AI, defining how tools are invoked, what scopes they require, and how credentials are managed.
Key strengths:
- Secure tool usage via OAuth2
- Metadata and context packaging
- Designed for external API invocation
Example: An agent using MCP to call a compliance-check API hosted on AWS Lambda, with credentials managed via Cognito.
2. Agent Communication Protocol (ACP)
ACP focuses on structured inter-agent communication. It formalizes messages with intents, plans, and memory references, enabling more advanced delegation, planning, and multi-step logic.
Key strengths:
- Clear message structures
- Intent-based reasoning
- Planner/thinker agent roles
Example: A planner agent sends an intent like {"intent": "summarize_document"} which downstream agents can interpret and act on.
3. Agent-to-Agent (A2A)
A2A represents the emerging protocol patterns from frameworks like LangGraph and CrewAI, focused on execution chaining. These agents hand off results, state, or tools in a tight feedback loop, optimized for responsiveness.
Key strengths:
- Streaming/low-latency agent graphs
- Role-defined execution flows
- Ideal for tool call orchestration
Example: LangGraph chain that processes text, extracts entities, and streams responses to a downstream verifier agent.
Matrix: Comparing MCP, ACP, and A2A
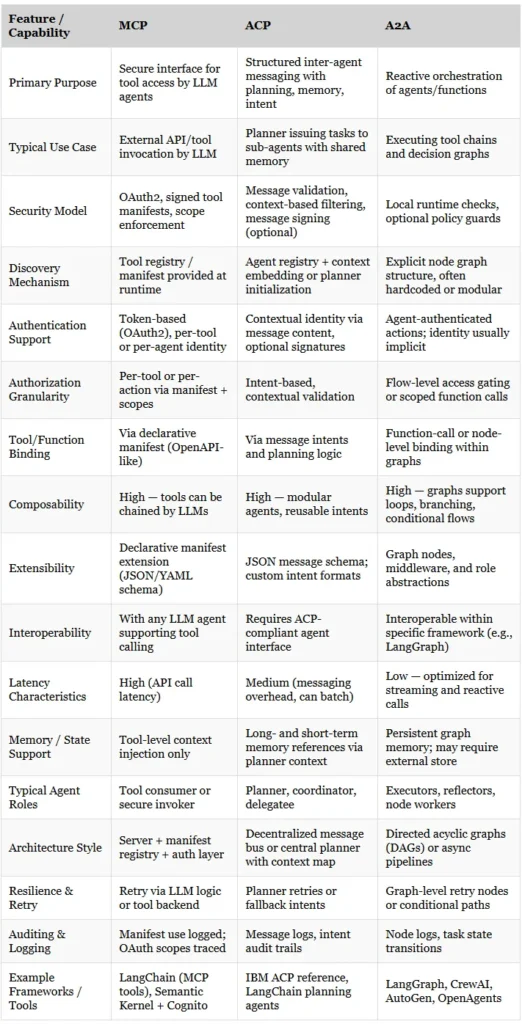
MCP and A2A are essential for context-aware, collaborative enforcement, where agents can negotiate task scopes, share domain insights, and avoid overlapping responsibilities during architecture reviews.
This article builds on that foundation. We now shift our focus from why these protocols matter to how to orchestrate them, transforming prompts into secure, structured actions across multiple agent roles.
From Prompt to Policy: Validating Cloud Architecture with AI Agents
To demonstrate how MCP, ACP, and A2A can be used together in a real-world system, we’ll walk through a practical use case focused on enforcing cloud architecture standards.
This scenario mirrors real-world workflows in DevSecOps, cloud governance, and architecture review boards. It illustrates how security and platform engineering teams can apply shift-left principles by using AI agents to automate infrastructure reviews, enforce internal policies, and detect misconfigurations early, before they reach production.
Goal:
“Review this CloudFormation template. Break it down into components, check for security best practices, and validate compliance with our internal deployment policy.”
Let’s walk through a working multi-agent system using all three protocols.
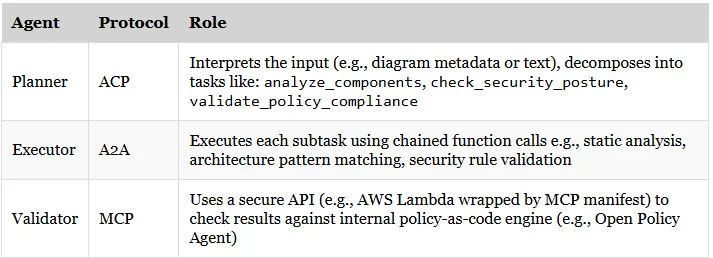
Agent Roles:
Execution Flow:
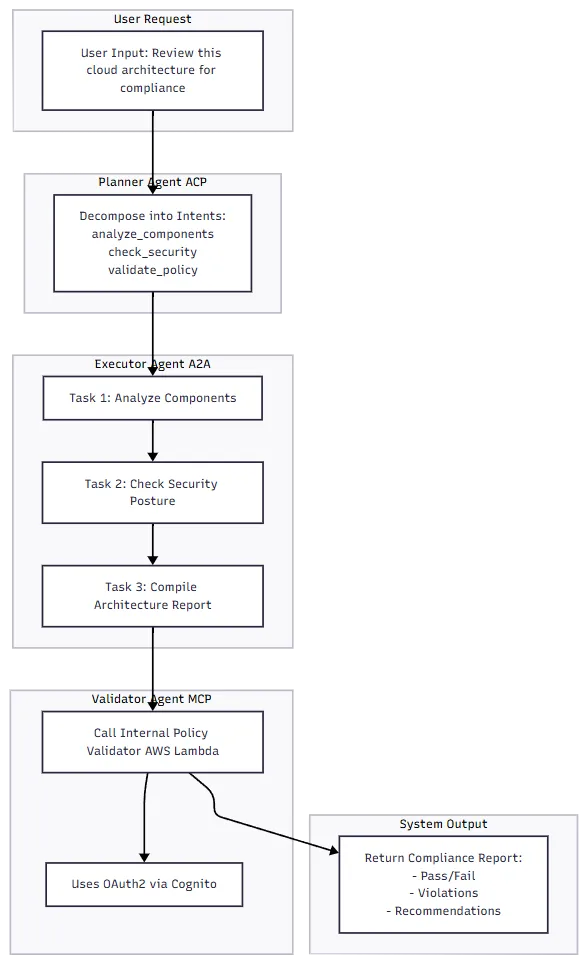
1. Prompt Input:
“Review this CloudFormation template. Identify its architectural components, evaluate them against our security best practices, and validate compliance with internal deployment policies.”
2. Planner Agent (ACP):
Breaks the request into structured task intents:
[
{ "intent": "analyze_components" },
{ "intent": "check_security_posture" },
{ "intent": "validate_policy_compliance" }
]3. Executor Agent (A2A):
- Runs static analysis on the architecture inputs
- Matches against known security patterns (e.g., public S3, IAM role sprawl)
- Assembles a full review report
4. Validator Agent (MCP):
- Sends report to a secure internal validation tool (OPA on AWS Lambda)
- Uses OAuth2 via Cognito for scoped access
- Returns pass/fail status and remediation guidance
5. Final Output:
- Aggregated results returned to the user: compliance status, flagged issues, and recommendations.
Conclusion: From Protocols to Playbooks
Most production-grade agent systems, like Raia, combine these protocols. MCP, ACP, and A2A each solve different layers of the multi-agent stack:
- MCP secures tool access.
- ACP drives high-level intent and planning.
- A2A executes workflows efficiently.
By combining them, you create modular, observable, and secure agent ecosystems, ready to scale across teams, APIs, and cloud-native deployments. This “layered stack” mirrors modern microservices combining REST, event buses, and API gateways.
Unlike REST or gRPC, none of these protocols are owned by an IETF or W3C-equivalent body yet. Most are community-driven, making early participation (and experimentation) valuable for shaping how open-source agent systems evolve.

